Experiencing a Breach? [email protected] | Safetech Blog
Protecting Your Inbox: What Are The Top Benefits of Managed Email Security
As you may know, email remains a critical tool for all of us. In fact, email communication is vital for more than 4 billion people worldwide. As of 2024, approximately 361.6 billion emails are sent daily worldwide. (Oberlo, 2023.)
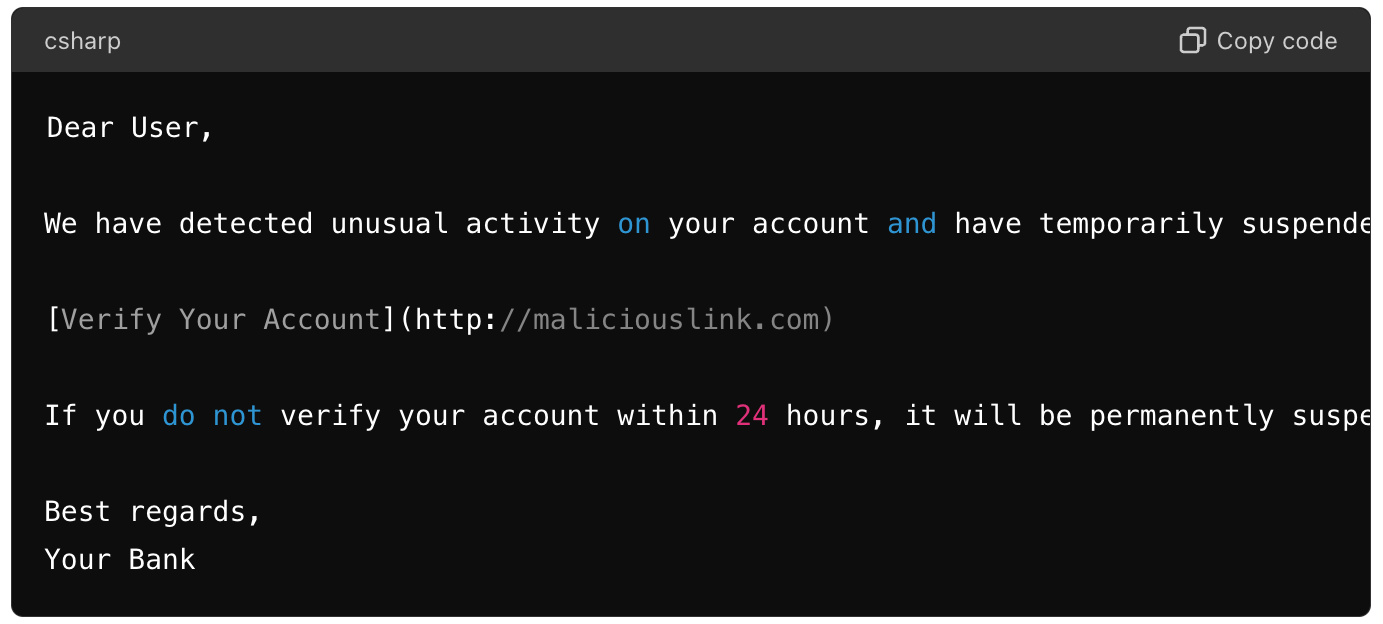
Explanation: The link leads to a fake website designed to look like the legitimate bank's site, where the user is asked to enter their login credentials. Once entered, these credentials are captured by the cybercriminals.
Spear Phishing
Example:
- Subject: Urgent: Invoice Payment Required
- Body:
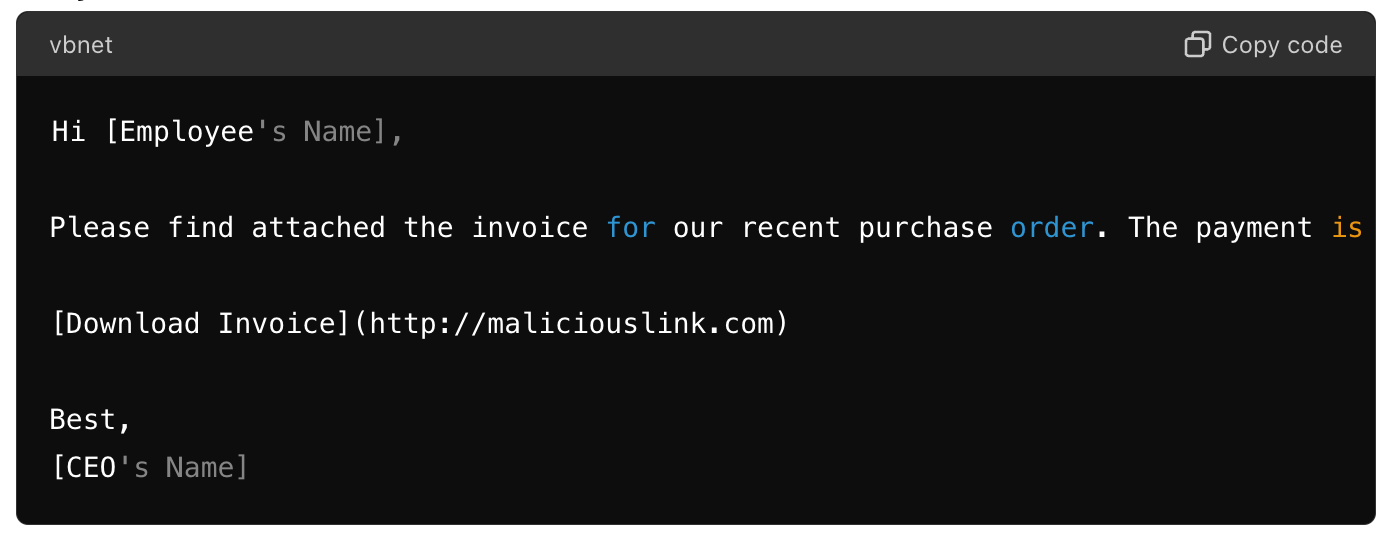
Explanation: This email appears to come from the CEO of the company, targeting a specific employee. The attachment or link might contain malware or direct the user to a site where they are prompted to enter sensitive information.
Email Spoofing
Example:
- Subject: Important Update from IT Department
- Body:

Explanation: The email appears to come from the IT department and instructs the recipient to update their password. The link directs to a fake site that captures the entered credentials.
Business Email Compromise (BEC)
Example:
- Subject: Urgent: Wire Transfer Request
- Body:
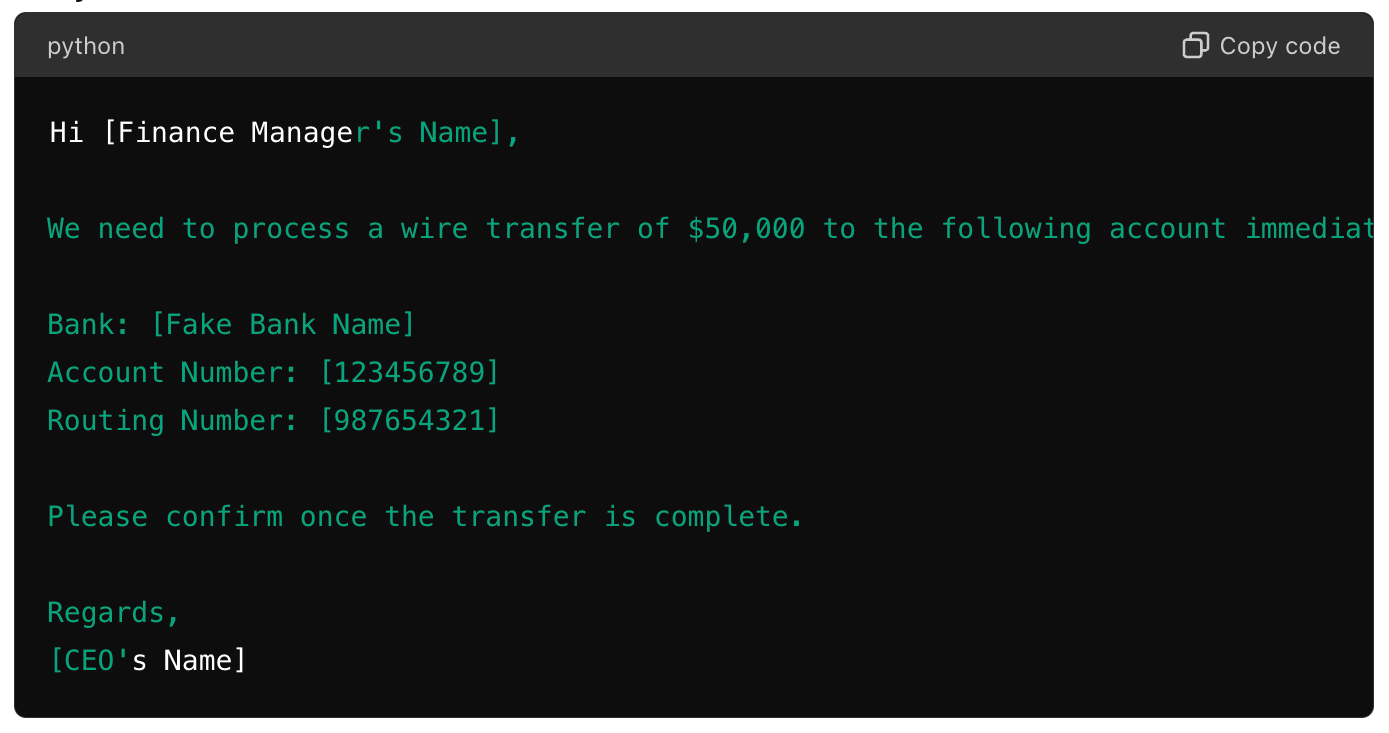
These examples illustrate how cybercriminals can use the most basic of email exploitations to deceive recipients into divulging sensitive information, downloading malware, or making unauthorised transactions. The common thread in all these examples is using social engineering tactics to exploit the recipient's trust and urgency.
Understanding Managed Email Security and why it’s important?
Managed email security involves outsourcing the management and protection of your email systems to a specialised service provider. These providers offer comprehensive solutions, including spam filtering, malware detection, phishing protection, encryption, and compliance management. By leveraging advanced technologies and expertise, managed email security services ensure your email communications and data are secure.
Benefits of Managed Email Security for your business
1. Enhanced Protection Against Phishing Attacks
Phishing attacks are among the most common and dangerous threats to email security. Cybercriminals use deceptive emails to trick recipients into revealing sensitive information, such as passwords or financial details. Managed email security employ advanced threat detection technologies to identify and block phishing attempts before they reach your inbox. These systems analyse email content, sender reputation, and other indicators to accurately detect phishing emails, reducing the risk of falling victim to such attacks.
2. Effective Spam Filtering
Spam emails are not only annoying but can also pose security risks. They often contain malicious links or attachments that can compromise your system if clicked or opened. Managed email security use sophisticated spam filtering techniques to keep your inbox free from unwanted and potentially harmful emails. These services ensure that only legitimate emails reach your inbox by continuously updating their spam filters based on emerging threats.
3. Advanced Malware Detection and Removal
Malware, such as viruses, worms, and ransomware, can be delivered via email attachments or links. Once inside your system, malware can cause significant damage, including data loss and system downtime. Managed email security solutions employ advanced malware detection and removal tools to scan email attachments and links for malicious content. These tools use heuristics, behavioural analysis, and signature-based detection to identify and eliminate malware threats, ensuring your email communications remain secure.
4. Data Encryption
Sensitive information transmitted via email, such as personal data, financial details, and confidential business information, must be protected from unauthorised access. Managed email security services provide end-to-end encryption for email communications, ensuring that only the intended recipients can read the content. Encryption protects your data from interception and eavesdropping, providing additional security for your email communications.
5. Compliance with Regulations
Many industries are subject to strict data protection regulations like GDPR, HIPAA, and PCI DSS. Compliance with these regulations requires robust email security measures to protect sensitive information. Managed email security services help businesses meet these regulatory requirements by implementing security controls, encryption, and monitoring capabilities. These services also provide audit trails and reporting features, making it easier to demonstrate compliance during audits.
6. Reduced IT Burden
Managing email security in-house can be resource-intensive and time-consuming. It requires continuous monitoring, updating, and responding to emerging threats. By outsourcing email security to a managed service provider, businesses can offload these responsibilities to experts specialising in email security. This allows IT teams to focus on core business activities while ensuring that email security is handled by professionals.
7. Improved Email Performance and Reliability
Managed email security services often include features that enhance email performance and reliability. These features can include email continuity services that ensure email delivery even during server outages and email archiving solutions that improve storage management and retrieval. By optimising email performance, managed email security services help businesses maintain efficient and reliable email communications.
8. Proactive Threat Intelligence
Cyber threats constantly evolve, with new attack vectors and techniques emerging regularly. Managed email security providers stay ahead of these threats by continuously updating their threat intelligence databases and employing proactive threat-hunting strategies. This proactive approach enables them to detect and mitigate emerging threats before they can impact your email systems, providing an added layer of protection.
9. Comprehensive Reporting and Analytics
Understanding the security landscape and the effectiveness of your email security measures is crucial for making informed decisions. Managed email security services provide comprehensive reporting and analytics features that offer insights into email threats, user behaviour, and overall security posture. These reports help businesses identify vulnerabilities, track security incidents, and measure the effectiveness of their email security strategies.
10. Cost-Effective Solution
Implementing and maintaining robust email security measures in-house can be expensive, especially for small and medium-sized businesses. Managed email security services offer a cost-effective alternative by providing access to advanced security technologies and expertise at a fraction of the cost. By leveraging economies of scale, managed service providers can deliver high-quality, affordable email security solutions for businesses of all sizes.
Implementing Safetech's Managed Email Security Solution
Safetech offers a comprehensive managed email security solution designed to protect your email communications from a wide range of threats. Here’s how Safetech’s solution can benefit your organisation:
Customised Security Solutions
Safetech understands that each organisation has unique security needs. Their managed email security solution is tailored to meet the specific requirements of your business. By conducting a thorough assessment of your email security posture, Safetech can design and implement a customised solution that provides optimal protection.
Advanced Threat Detection and Prevention
Safetech’s managed email security solution leverages cutting-edge technologies to detect and prevent advanced threats. This includes real-time threat intelligence, machine learning algorithms, and behavioural analysis to identify and block phishing attempts, malware, and other malicious activities. By staying ahead of emerging threats, Safetech ensures that your email communications remain secure.
Robust Spam Filtering
Safetech’s solution includes advanced spam filtering capabilities that keep your inbox free from unwanted and potentially harmful emails. By continuously updating their spam filters based on the latest threat intelligence, Safetech ensures that only legitimate emails reach your inbox, reducing the risk of falling victim to spam-related threats.
End-to-End Encryption
Safetech’s managed email security solution provides end-to-end encryption for email communications, ensuring that sensitive information remains protected from unauthorised access. This encryption technology ensures that only the intended recipients can read the email content, safeguarding your data from interception and eavesdropping.
Compliance Support
Safetech’s managed email security solution helps businesses meet regulatory requirements by implementing necessary security controls and monitoring capabilities. With features such as encryption, audit trails, and reporting, Safetech ensures that your email communications comply with data protection regulations, making it easier to demonstrate compliance during audits.
24/7 Monitoring and Support
Cyber threats can occur anytime, so Safetech offers 24/7 monitoring and support as part of its managed email security solution. Their team of experts continuously monitors your email systems for suspicious activities and responds promptly to any security incidents. This round-the-clock monitoring ensures that your email communications are always protected.
Scalable and Flexible Solution
Safetech’s managed email security solution is designed to scale with your business. Whether you have a small team or a large organisation, Safetech can accommodate your email security needs. Their flexible solution allows you to add or remove users and adjust security settings as your business evolves, ensuring your email security remains effective as you grow.
Summary
Protecting your email communications is paramount. Managed email security solutions offer comprehensive protection against phishing attacks, spam, malware, and other threats, ensuring your inbox remains safe and secure. By outsourcing email security to a specialised service provider like Safetech Innovations, businesses can benefit from enhanced protection, reduced IT burden, and improved compliance with regulations. Investing in managed email security is a smart move to safeguard your communications and protect your sensitive information.
Reference:
Oberlo, 2023. How Many Emails Are Sent Per Day in 2024? https://www.oberlo.com/statistics/how-many-emails-are-sent-per-day









More protection. Less tech.
We're removing the complexity within your security tech stack. Forget alert fatigue and let Safetech streamline and simplify your security posture.
NAVIGATION
STAY CONNECTED
You need a helping hand with your project?
Thank you for signing up to our email newsletter.
Please try again later


No. 12-14 Frunzei Street, Frunzei Center, 1st-3rd Floor, 2nd District, 021533, Bucharest, Romania
Safetech Innovations Global Services LTD. All rights reserved. - We are a UK company. Registration number: 13901115. In the USA we act under Safetech Innovations USA Inc, a Virginia corporation registered under 11506098. ICO (UK) ZB425433
Professional Indemnity Insurance | Public and Product Liability Insurance *Information can be provided on request










