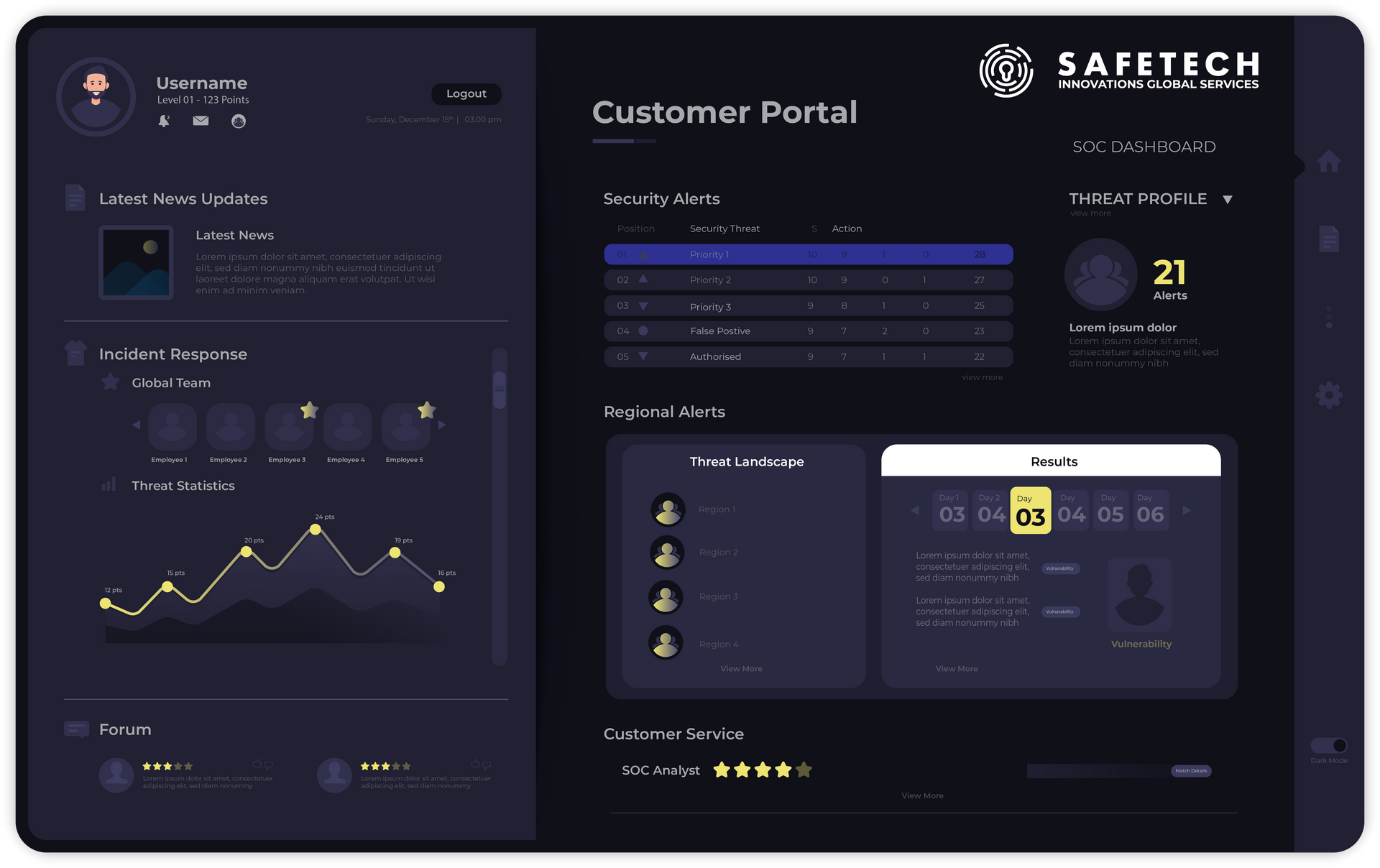
Proactive protection and detection with Safetech Innovation's advanced vulnerability scanning
Our proactive vulnerability scanning is crucial not only for detecting existing weaknesses within your organisation but also for anticipating potential future security issues, allowing for timely remediation and strengthening of your cyber defences.
How can you protect your business without knowing where your vulnerabilities are?
We all know that vulnerability scanning is a vital process in cybersecurity, and essential for maintaining the integrity and security of any digital infrastructure.
In today's fast-paced digital world, where cyber threats are increasingly sophisticated and pervasive, vulnerability scanning stands as a primary line of defence for businesses and organisations of all sizes.
Why is vulnerability scanning vital for your cyber protection?
Got a question? We’re here to help.