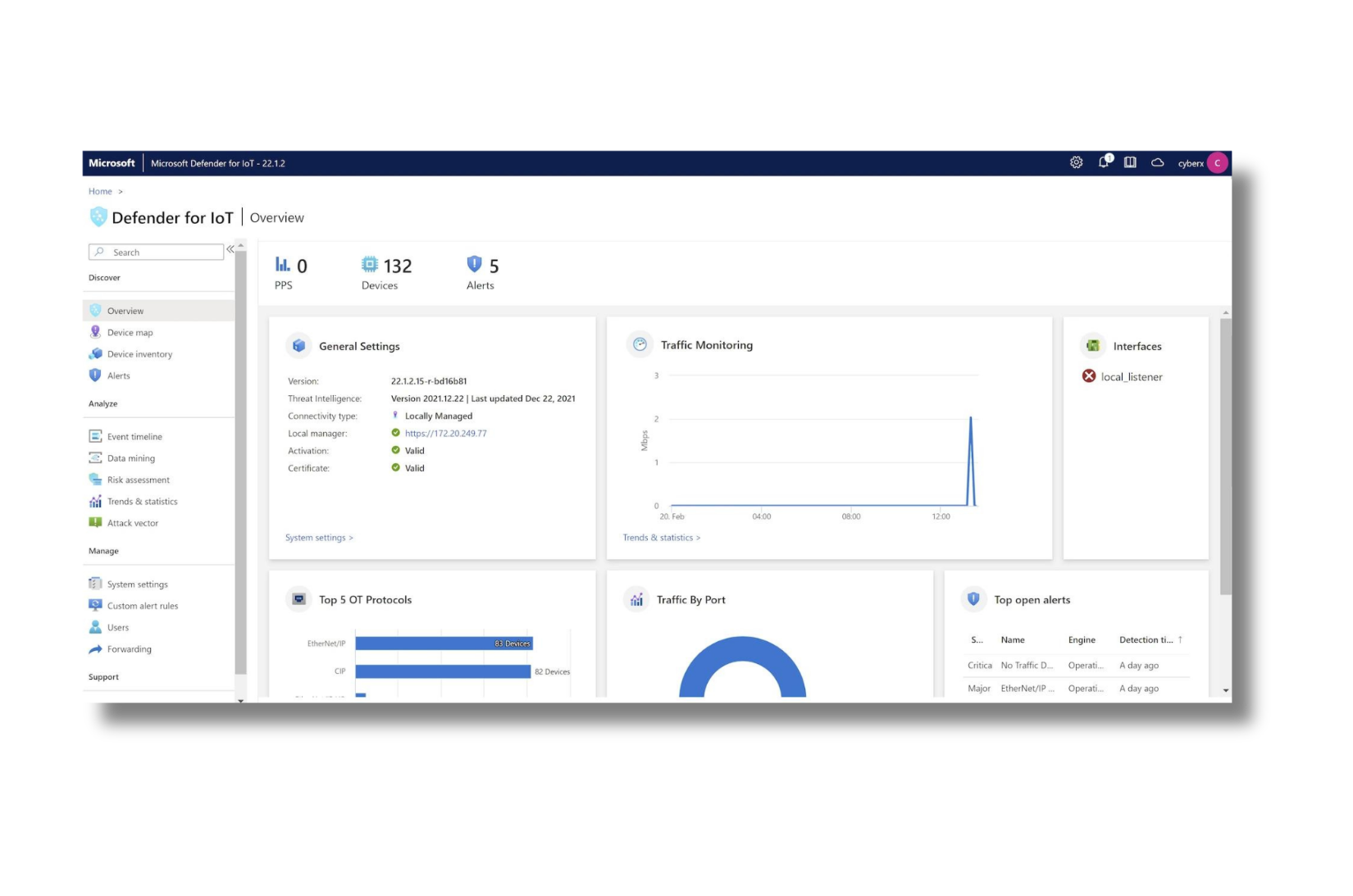
Cyber security of OT and IoT Environments
Operational Technology (OT) cybersecurity is crucial because the infrastructures it manages are essential for basic services such as electricity, water supply, transport, and industrial production. A cyber attack on these systems can lead to catastrophic consequences, including widespread service disruptions, physical damage, and threats to public safety.
Protecting OT and Industrial Control Systems (ICS) with robust cybersecurity measures is vital to safeguard these critical infrastructures.

IoT CHALLENGES
As the number of IoT devices continues to grow and they become more integrated into various aspects of our lives, it becomes crucial to ensure their security to prevent potential risks and vulnerabilities.